Get ahead
VMware offers training and certification to turbo-charge your progress.
Learn moreWe're pleased to announce that the first milestone of Spring Security 3.0 is now available for download. The release is also available through the Maven milestone repository at http://maven.springframework.org/milestone. As with Spring 3.0, this is the first release which requires a minimum JDK 1.5 to run and also require Spring 3.0, so you should get hold of the Spring 3.0.0.M3 release if you aren't already using it. So what's new and what has changed in this release?
<http use-expressions="true">
<intercept-url pattern="/secure/**" access="hasRole('ROLE_SUPERVISOR') and hasIpAddress('192.168.1.0/24')" />
...
</http>;
The built–in hasRole('ROLE_SUPERVISOR') expression is nothing fancy – it just checks the current user's authority list and returns true if they have the given role. But we've added an extra expression to specify that the IP address making the request must be in the range defined by the subnet/mask argument. This may or may not be of practical use depending on your network setup, but it illustrates how powerful the expression-based approach is. The list of security attributes which was previously contained in the "access" XML attribute has been replaced by a boolean expression. If it evaluates to "true" access will be granted. If it evaluates to "false", access will be denied.
<global-method-security pre-post-annotations="enabled"/>
The most obviously useful annotation is @PreAuthorize which controls whether a method can actually be invoked or not. For example (from the "Contacts" sample application):
@PreAuthorize("hasRole('ROLE_USER')")
public void create(Contact contact);
which means that access will only be allowed for users with the role "ROLE_USER". Nothing new here. But what about:
@PreAuthorize("hasPermission(#contact, 'admin')")
public void deletePermission(Contact contact, Sid recipient, Permission permission);
Here we're actually using a method argument as part of the expression to decide whether the current user has the "admin" permission for the given contact. The hasPermission() expression is linked into the Spring Security ACL module through the application context (see the Contacts sample configuration for how this is achieved). You can access any of the method arguments by name as expression variables, provided your code has debug information compiled in. Any Spring-EL functionality is available within the expression, so you can also access properties on the arguments. For example, if you wanted a particular method to only allow access to a user whose username matched that of the contact, you could write
@PreAuthorize("#contact.name == principal.name)")
public void doSomething(Contact contact);
Here we are accessing another built–in expression, which is the "principal" of the current Spring Security Authentication object obtained from the security context. You can also access the Authentication object itself directly using the expression name "authentication". Authorization can also be performed after the method call has taken place, using the @PostAuthorize annotation. To access the return value from a method, use the built–in name "returnObject" in the expression.
@PreAuthorize("hasRole('ROLE_USER')")
@PostFilter("hasPermission(filterObject, 'read') or hasPermission(filterObject, 'admin')")
public List getAll();
When used with the @PostFilter annotation, Spring Security iterates through the returned collection and removes any elements for which the supplied expression is false. The name "filterObject" refers to the current object in the collection. You can also filter before the method call, using @PreFilter, though this is probably a less common requirement. The syntax is just the same, but if there is more than one argument which is a collection type then you have to select one by name using the "filterTarget" property of this annotation.
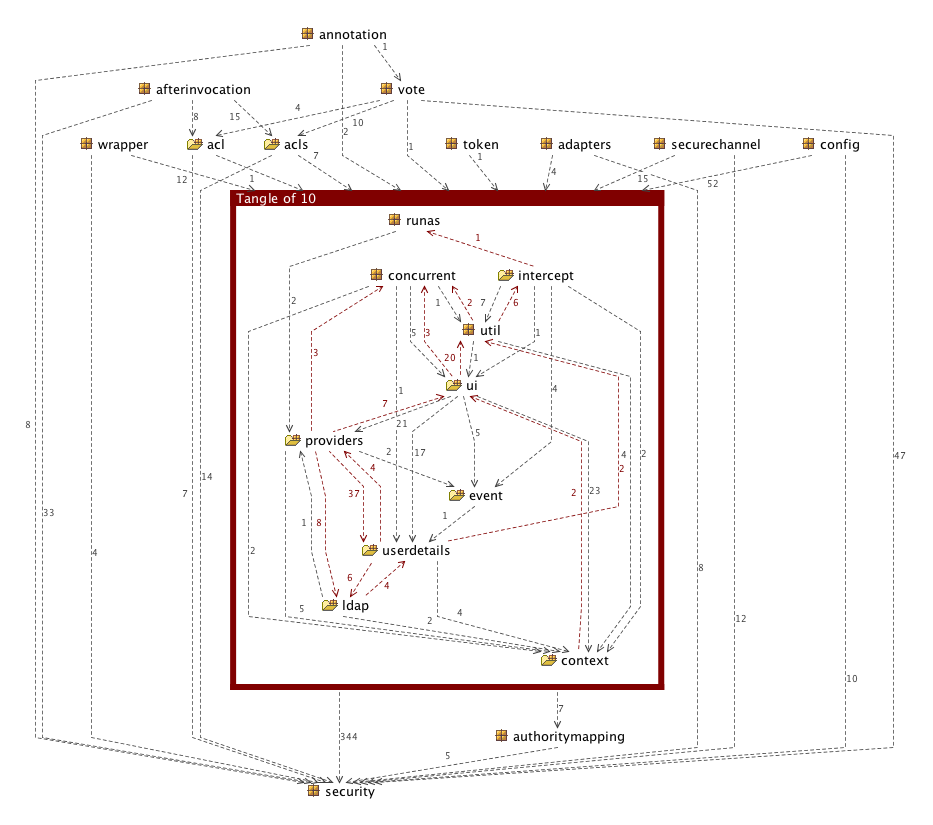
Spring Security 2.0.4 Package Structure
| Jar Name | Description | When to use | Root Package(s) |
|---|---|---|---|
| spring-security-core | Core authentication and access-contol classes and interfaces. Remoting support and basic provisioning APIs. | Required by any application which uses Spring Security. Supports standalone applications, remote clients, method (service layer) security and JDBC user provisioning. | org.springframework.security.core,
org.springframework.security.access,
org.springframework.security.authentication,
org.springframework.security.provisioning,
org.springframework.security.remoting |
| spring-security-web | Filters and other web-security infrastructure and related code. Anything with a servlet API dependency. | If you require Spring Security web authentication services and URL-based access-control | org.springframework.security.web |
| spring-security-config | Namespace parsing code. | If you are using the Spring Security XML namespace. | org.springframework.security.config |
| spring-security-ldap | LDAP authentication and provisioning code. | If you need to use LDAP authentication or manage LDAP user entries. | org.springframework.security.ldap |
| spring-security-acl | Domain object ACL implementation. | If you need to apply security to specific domain object instances within your application. | org.springframework.security.acls |
| spring-security-cas-client | Spring Security's CAS client integration. | If you want to use Spring Security web authentication with a CAS single sign-on server. | org.springframework.security.cas |
| spring-security-openid | OpenID web authentication support. | If you need to authenticate users against an external OpenID server. | org.springframework.security.openid |
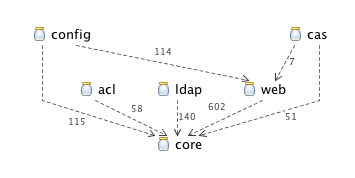
Spring Security 3.0.0.M1 Jar Dependencies
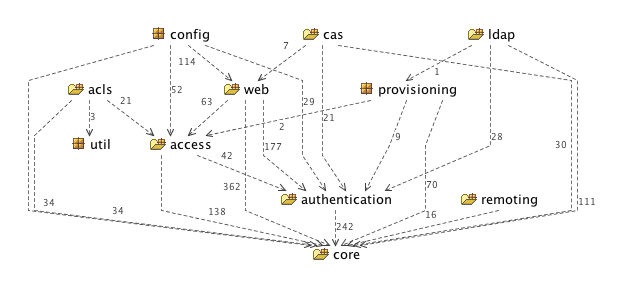
Spring Security 3.0.0.M1 Package Structure
core package and sub packages contain the basic classes and interfaces which are used throughout the framework and the other two main packages within the core jar are authentication and access. The access package containst access-control/authorization code such as the AccessDecisionManager and related voter-based implementations, the interception and method security infrastructure, annotation classes and support for Spring Security 3.0's expression-based access control. The authentication package contains the AuthenticationManager and related classes (such as authentication exception classes), the simple DAO-based authentication provider and password-encoders.
The project web site has also been updated. The FAQ has some new questions and there's a new page with links to presentation videos and online articles. Please take a look and let us know if there's anything you'd like to see there (an external Security links page is already in the works).
There's still a lot of work to be done for Spring Security 3, but we hope you'll try out this milestone release and provide some feedback on the new expression language support. You can find a full list of the changes to date in the Jira ChangeLog and you'll also find links to the current project roadmap there.
The Community Forum is the best place to ask questions on using Spring Security or to start discussions on new features. Alternatively, if you find something amiss, you can raise a Jira Issue.
We hope you enjoy using Spring Security.